Introduction
Although current efforts increasingly aim to minimize the use of passwords – for example, through passkeys – passwords will remain with us for the foreseeable future. They are especially essential in the realm of system access and accounts, where authentication via a password or secret remains the most common method.
For decades, we’ve been taught to create passwords using a combination of numbers, uppercase and lowercase letters, and special characters. But is this really the best approach? Are there perhaps other ways to generate a secure password? In this post, we will explore these questions.
Password Entropy
A secure password is defined by a level of complexity that makes it economically impractical for attackers to crack. The complexity of a password can be increased in two ways – either through a larger character set or by increasing the password length.
To calculate password complexity, the concept of password entropy is used. This is measured in bits and indicates the actual strength of a password.
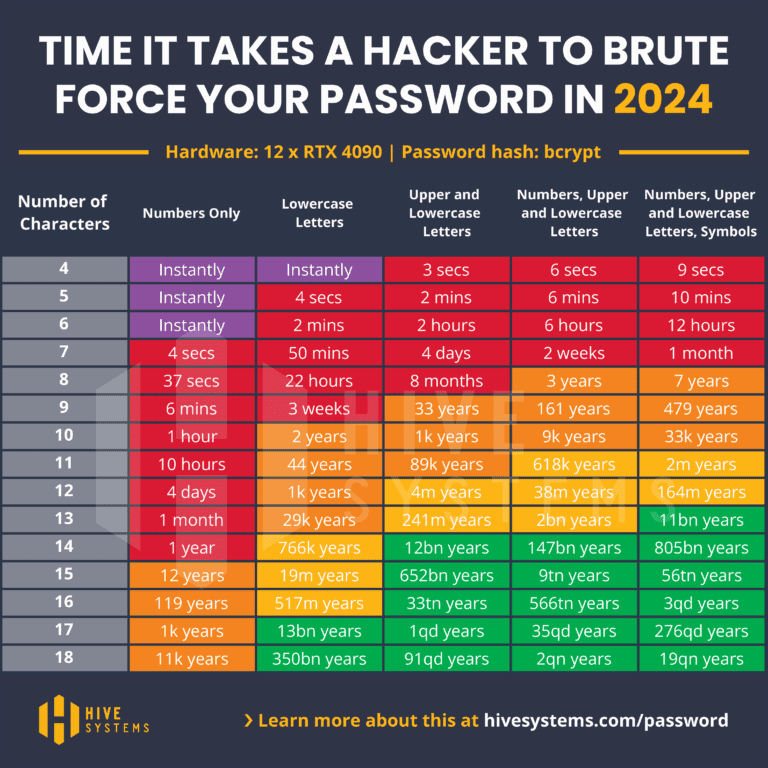
Before diving deeper into this, let’s first take a look at how long it takes to crack passwords with different character sets and lengths. The table below is published annually by Hive Systems:
It is based on a so-called brute-force attack, meaning that all possible combinations are systematically tested. More about the different types of attacks will be covered in the next chapter.
So, what do these numbers from the table mean? Does this mean that it always takes exactly that long to crack a password with the corresponding complexity?
No, the values in the table represent a worst-case scenario. This means that all possible combinations must be tested to find the correct one.
For example: A password with 8 uppercase and lowercase letters could take 8 months to crack in the worst case. However, it’s also possible that the password could be found much earlier. The more complex a password is, the less likely it is that it will be randomly cracked quickly. This is why it’s important to allow some flexibility in complexity.
What can we learn from the table?
The table shows that a secure password can be created with relatively few characters when a complex character set is used—comprising uppercase and lowercase letters, numbers, and special characters.
More importantly, we also see that it is possible to create secure passwords with a smaller character set.
For example, a password made solely of numbers, when 18 characters long, can be considered secure.
Why is that?
This is where password entropy comes into play.
Let’s take a password with 10 characters and a character set consisting of uppercase and lowercase letters, numbers, and symbols (a total of 32 characters). This password has an entropy of approximately 66 bits, or about 1.8 × 10¹⁹ possibilities (18,446,744,073,709,551,616).
Now, comparing this with an 18-character password made only of numbers, we get an entropy of 60 bits—just 6 bits less.
So, we conclude: The entropy of a password is what matters most, not necessarily the use of different character types or symbols.
Principles for Secure Passwords
Before we dive into what really matters when creating secure passwords, let’s first take a look at some basic best practices:
Attack Types
To crack passwords, attackers use various methods that differ in complexity and effort. Phishing and social engineering have been deliberately excluded as these attack methods have nothing to do with password complexity. Here are the most common attack types:
Brute-Force Attack
In a brute-force attack, all possible combinations of characters are systematically tested until the correct password is found. This is the method most people associate with password cracking, though it is rarely used by attackers.
Advantage for attackers: Guaranteed success as long as there is sufficient time and computational power.
Disadvantage for attackers: Very time- and resource-intensive, especially with passwords that have high entropy (long and complex combinations).
Mask Attack
A mask attack is an optimized version of a brute-force attack. Instead of testing all possible combinations of characters, attackers use specific patterns or rules to guess passwords. These rules are often based on common behaviors and known password formats, such as those frequently used in practice or when certain information about a password (such as length or character set) has already been leaked through an enumeration attack.
Advantage for attackers: Significantly faster than a brute-force attack.
Disadvantage for attackers: Still very time- and resource-intensive depending on the level of information available.
Dictionary Attack
In a dictionary attack, passwords are tested using dictionaries or precompiled lists of common words. This method is faster than a brute-force attack because it only tests likely passwords.
Advantage for attackers: Password can usually be cracked within minutes if it is on the list.
Disadvantage for attackers: Works only on weak passwords that are based on dictionary entries or leaked passwords.
Risk: These lists are constantly updated and optimized.
Creating Secure Passwords
Based on the insights we’ve gained, how should we create passwords?
To answer this question, we need to distinguish between different use cases:
User Passwords for Manual Entry
Some passwords must be manually entered by the user. With consistent use of a password manager, this should generally only be the master password of the password manager itself. Regardless of the technological measures used for digital account management, there will always be at least one account or password that must be entered manually. This master password should be something you can remember easily. For additional security, it can be backed up in the password manager.
From the previous insights, we know that special characters or symbols are not strictly necessary to make a password secure. For this particular use case, choose a password that is easy to remember, consists of as many characters as possible, and has no personal connection to you. A proven method is using a passphrase— a password made up of multiple words.
Mindynamic recommends creating a passphrase of 16 characters or more, without special characters, to optimally combine user-friendliness, security, and memorability.
User Passwords in the Password Manager
Every password manager allows you to configure a standard policy for the password generator. Since many services still require special characters and often impose a maximum password length, we recommend a standard policy of 14 characters, incorporating uppercase and lowercase letters, numbers, and special characters. It is advisable to limit the special characters to those that are unproblematic (e.g., !, ?, $, *, #, +, @) to avoid compatibility issues.
This policy ensures a high level of security while meeting the requirements of most platforms.
System Accounts and Service Principals
Since these accounts are often used for autonomous authentication by programs, scripts, and services where multi-factor authentication is not possible, we recommend using passwords with at least 20 characters. These should consist of uppercase and lowercase letters and numbers, but should not include special characters. Special characters might cause issues, as they could be interpreted by executing programs as “special characters,” potentially interfering with the correct execution.
Are you unsure if your chosen password is sufficiently secure? We recommend using the password entropy calculator from Omnicalculator. This tool helps you evaluate the strength of your password: Password Entropy Calculator
Password Changes
Some of you might be wondering about the still commonly practiced method of periodically changing passwords to enhance security.
We will explore this and other topics related to the implementation of security policies in a detailed follow-up article.
Stay tuned!
Conclusion
Brute-force attacks are rarely used today because they are resource-intensive, costly, slow, and often ineffective. Instead, attackers prefer phishing and social engineering attacks. However, if you use a weak or leaked password, it can be cracked in a short amount of time. Therefore, using secure passwords remains essential.
Secure passwords do not necessarily need to contain an exceptionally large character set. What is far more crucial for security is the length of the password, as more characters have a much greater impact on entropy and, thus, on resistance to attacks than the variety of characters used.
Unfortunately, most services still check the character set used, such as uppercase and lowercase letters, as well as the inclusion of symbols, instead of evaluating the actual entropy of the password.
The updated password guidelines from the National Institute of Standards and Technology (NIST) support the approaches discussed in this article. A summary of these guidelines and their key changes can be found here: NIST Password Guidelines: Updated as per the Recent Version
Empfehlungen
As mentioned earlier, using a good password manager is essential. Mindynamic recommends Bitwarden for the following reasons:
For Enterprise Users, Bitwarden also offers:
By using Bitwarden, you can ensure your passwords are managed securely, both individually and across your organization.


Leave a Reply